Introduction to Microsoft Defender Credential Guard
Microsoft Defender Credential Guard is a security feature designed to protect sensitive information in Windows environments. By leveraging virtualization-based security, it isolates secrets such as user credentials from potential threats. This isolation is crucial for preventing sophisticated attacks such as Pass-the-Hash and Pass-the-Ticket, which aim to steal and misuse credentials.
Credential Guard plays a significant role in enhancing the overall security posture of an organization. In traditional environments, credentials are stored in the Local Security Authority (LSA), making them susceptible to extraction by malicious actors who gain administrative privileges. However, with Credential Guard, these credentials are stored in a secure, isolated container, significantly reducing the attack surface.
The importance of Credential Guard cannot be overstated, as it provides a robust defense mechanism against lateral movement within a network. By ensuring that credentials are not easily accessible, it mitigates the risk of attackers leveraging stolen credentials to move from one system to another, thereby containing potential breaches.
In addition to protecting against credential theft, Microsoft Defender Credential Guard also simplifies compliance with various security standards and regulations. Organizations are increasingly required to demonstrate strong measures for protecting sensitive information, and implementing Credential Guard is a step towards meeting these requirements.
Deploying Credential Guard is straightforward, especially with the use of PowerShell. PowerShell provides a powerful and flexible tool for administrators to configure and manage Credential Guard settings across multiple systems efficiently. Understanding how to utilize PowerShell for this purpose is essential for maintaining a secure and compliant environment.
In the subsequent sections, we will delve into the specifics of enabling Microsoft Defender Credential Guard using PowerShell. This guide aims to provide a comprehensive overview of the steps involved, ensuring that administrators can implement this critical security feature effectively.
Before enabling Microsoft Defender Credential Guard using PowerShell, it is essential to ensure your system meets the necessary prerequisites and system requirements. This security feature, designed to protect credentials from theft, is supported on specific Windows versions and requires particular hardware features to function correctly.
Microsoft Defender Credential Guard is compatible with Windows 10 Enterprise, Windows 10 Education, and Windows Server 2016 and later versions. These operating systems offer the necessary infrastructure to support this advanced security feature. Ensuring your system runs one of these supported versions is the first step in the process.
In addition to the correct Windows version, certain hardware features are mandatory. A Trusted Platform Module (TPM) version 1.2 or 2.0 is required. TPM is a hardware-based security feature that helps protect and store cryptographic keys, crucial for Credential Guard’s functionality. Secure Boot, another vital requirement, ensures that only trusted software is loaded during the boot process. It helps prevent malicious software from loading during the system start-up. Additionally, the system must be configured to use Unified Extensible Firmware Interface (UEFI) instead of the legacy BIOS. UEFI provides a more secure interface between the operating system and firmware, enhancing the overall security posture.
Moreover, it is critical to ensure that your system has the latest updates and patches installed. Microsoft frequently releases updates that address security vulnerabilities and improve system stability. Applying these updates ensures that your system benefits from the latest security enhancements and is capable of supporting Credential Guard.
By confirming that your system meets these prerequisites and system requirements, you can effectively proceed with enabling Microsoft Defender Credential Guard using PowerShell, thereby enhancing the security of your credentials against potential threats.
Preparing the Environment for Credential Guard
Before enabling Microsoft Defender Credential Guard with PowerShell, it is imperative to prepare the environment adequately. Ensuring that the system meets all prerequisites is the first step towards a successful implementation. This preparatory phase includes updating the BIOS/UEFI firmware, enabling Secure Boot, verifying the Trusted Platform Module (TPM) status, and ensuring overall system compatibility.
Firstly, updating the BIOS/UEFI firmware is crucial. Most hardware manufacturers provide firmware updates that can be downloaded from their official websites. To check the current BIOS/UEFI version, press Win + R, type msinfo32, and press Enter. The “System Information” window will display the BIOS/UEFI version and date. Compare this information with the latest version available on the manufacturer’s website and proceed with the update if necessary.
Next, enable Secure Boot, a security standard developed to ensure that a device boots using only software trusted by the Original Equipment Manufacturer (OEM). To enable Secure Boot, restart the computer and enter the BIOS/UEFI settings (usually by pressing a designated key such as F2, F10, DEL, or ESC during the boot process). Navigate to the Boot or Security tab and ensure Secure Boot is enabled. Save changes and exit the BIOS/UEFI setup.
Enabling Credential Guard with PowerShell
To enable Microsoft Defender Credential Guard using PowerShell, it’s essential to understand the sequence of commands required and their respective functionalities. Credential Guard leverages virtualization-based security to protect secrets in a virtualized environment, safeguarding them from potential theft or misuse. Below is a detailed, step-by-step guide to achieving this using PowerShell.
You need to enable Hyper-V, which is crucial for creating the virtual secure mode. Use this command:
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Hyper-V-All
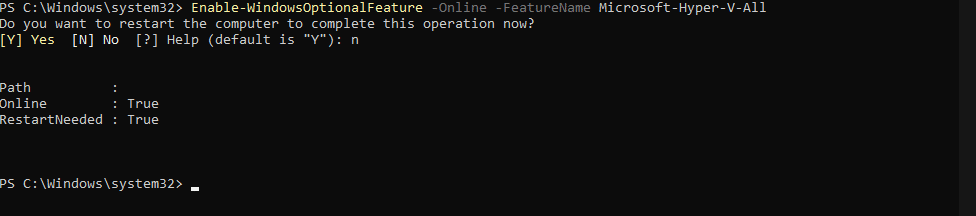
This command ensures that all components of Hyper-V are installed. As with the previous step, you may be prompted to restart your system.
Following the activation of Hyper-V, you can now proceed to enable Credential Guard. Execute the following PowerShell command:
Set-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\DeviceGuard" -Name "EnableVirtualizationBasedSecurity" -Value 1
This command sets the registry key to enable VBS. You also need to specify that Credential Guard should be enabled. Execute:
Set-ItemProperty -Path "HKLM:SYSTEM\CurrentControlSet\Control\Lsa" -Name "LsaCfgFlags" -Value 1
The command above modifies the registry to turn on Credential Guard. You might need to restart your computer once more to apply these changes successfully.
Finally, it’s advisable to confirm that Credential Guard is active. Use the following PowerShell command:
Get-CimInstance -ClassName Win32_DeviceGuard -Namespace root\Microsoft\Windows\DeviceGuard
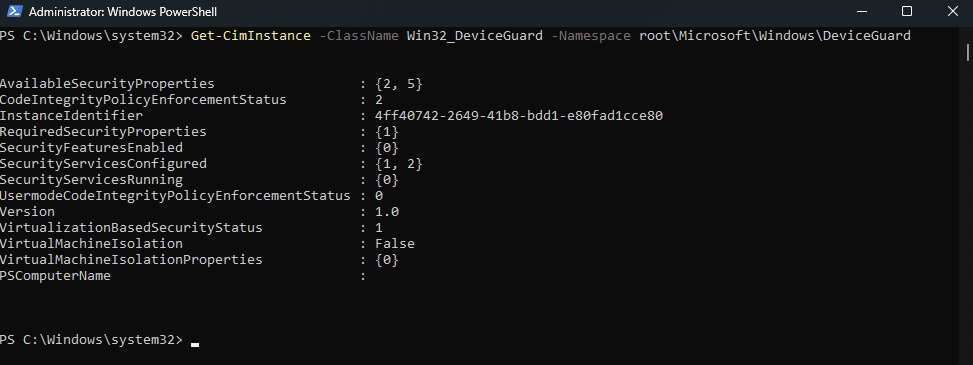
This will retrieve the status of Device Guard, including Credential Guard, providing confirmation that it is enabled and running correctly.
By following these steps, you can efficiently enable Microsoft Defender Credential Guard using PowerShell, enhancing your system’s security posture.
Verifying Credential Guard Activation
Once you have enabled Microsoft Defender Credential Guard, it is crucial to verify that it is functioning correctly. This can be achieved through a few methods, including utilizing PowerShell commands, the Device Guard and Credential Guard hardware readiness tool, and examining system logs.
To start with PowerShell, you can run the following command to check if Credential Guard is enabled on your system:
Get-CimInstance -ClassName Win32_DeviceGuard -Namespace root\Microsoft\Windows\DeviceGuard
This command retrieves information about Device Guard and Credential Guard from your system. The output will include various properties, but focus on the SecurityServicesConfigured and SecurityServicesRunning properties. These should include the value 2, indicating that Credential Guard is configured and running.
Another method of verification is using the Device Guard and Credential Guard hardware readiness tool. This tool is available from Microsoft and provides a comprehensive check of your system’s compatibility and the status of Credential Guard. After downloading and running the tool, it will generate a report detailing the status of Credential Guard. If Credential Guard is active, the report will explicitly state that it is running.
System logs can also provide confirmation of Credential Guard activation. Open the Event Viewer and navigate to Applications and Services Logs -> Microsoft -> Windows -> DeviceGuard. Look for events with the ID 7010, which indicate that Credential Guard has started successfully. The presence of this event confirms that Credential Guard is operational.
By using these methods, you can confidently verify that Microsoft Defender Credential Guard is active on your system, ensuring added security for your credentials. Utilizing PowerShell alongside other verification tools provides a robust approach to confirming the operational status of Credential Guard, thereby enhancing your system’s security posture.
Troubleshooting Common Issues
Enabling Microsoft Defender Credential Guard using PowerShell is generally straightforward, but users may encounter several common issues that can impede the process. Understanding these issues and their respective solutions can help ensure a smoother experience.
Hardware Compatibility Issues
One frequent problem involves hardware compatibility. Credential Guard requires specific hardware features, such as virtualization-based security (VBS) and UEFI firmware with Secure Boot. If your system lacks these features, PowerShell commands to enable Credential Guard will fail. For example, you may encounter the error message:
“Credential Guard cannot be enabled because the system does not support Secure Boot.”
To resolve this, check your system’s BIOS/UEFI settings to ensure that Secure Boot is enabled. Additionally, verify that your CPU supports virtualization and that it is enabled in the BIOS/UEFI.
Software Conflicts
Another common issue stems from software conflicts. Certain applications, particularly those involving virtualization, can interfere with Credential Guard. For example, you might see an error message like:
“Credential Guard cannot be enabled because Hyper-V is not installed or is disabled.”
To troubleshoot this, ensure that Hyper-V is installed and enabled on your system. You can use PowerShell to check the status and enable Hyper-V if necessary:
Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Hyper-V-All
Additionally, verify that there are no conflicts with other virtualization software, such as VMware or VirtualBox. Disabling or uninstalling these applications may be required.
Misconfigurations
Misconfigurations in the system settings can also cause issues when enabling Credential Guard. For instance, incorrect Group Policy settings or registry entries can prevent successful activation. If you encounter an error like:
“Credential Guard cannot be enabled due to incorrect Group Policy settings.”
Review the Group Policy settings related to Credential Guard. Navigate to Computer Configuration > Administrative Templates > System > Device Guard and ensure that the relevant policies are correctly configured. You can also use PowerShell to verify and correct registry entries:
Set-ItemProperty -Path "HKLM:Software\Policies\Microsoft\Windows\DeviceGuard" -Name "EnableVirtualizationBasedSecurity" -Value 1
By addressing these common issues related to hardware compatibility, software conflicts, and misconfigurations, users can more effectively enable Microsoft Defender Credential Guard using PowerShell, ensuring enhanced security for their credentials.
Best Practices and Maintenance
Ensuring a secure environment with Microsoft Defender Credential Guard enabled involves adhering to a series of best practices and maintenance routines. Firstly, regular updates are paramount. It’s crucial to keep your operating system, firmware, and all related security tools updated. Regularly check for firmware updates from your hardware manufacturer and apply them promptly to mitigate vulnerabilities that could be exploited by attackers.
Monitoring and auditing practices should also be an integral part of your security strategy. Regularly review system logs and audit trails for any unusual activities. PowerShell scripts can be employed to automate the collection and analysis of these logs, making the process more efficient. By actively monitoring your system, you can quickly identify and respond to potential security threats.
Applying security patches as soon as they become available is another critical practice. Security patches address vulnerabilities that could be exploited by malicious actors, so it’s vital to apply them without delay. PowerShell can be used to automate the deployment of these patches, ensuring your system remains secure without requiring manual intervention.
In addition to enabling Credential Guard, it’s essential to ensure that other security features are properly configured and up to date. This includes antivirus software, firewalls, and intrusion prevention systems. Regularly check that these features are active and receiving the latest updates to provide comprehensive protection for your system.
Lastly, conducting regular security assessments and vulnerability scans can help identify potential weaknesses in your environment. Use PowerShell scripts to facilitate these assessments, ensuring that your system is continually evaluated for potential risks. By following these best practices and maintaining a proactive security posture, you can significantly enhance the security of your environment with Microsoft Defender Credential Guard enabled.
We hope you find it helpful.
