As an ethical Hacker, we are always looking for devices that are available on the network that we can scan. NMAP does a brilliant job by telling us which hosts are alive on the network but so do many other applications such as Angry IP Scanner, SolarWinds etc.
If you are not using any of these enterprise applications or tools such as NMAP are blocked, you can use PowerShell to find available hosts on the network and the script I put together does try and tie a hostname with the IP address but we know that some devices do not always give us a hostname.
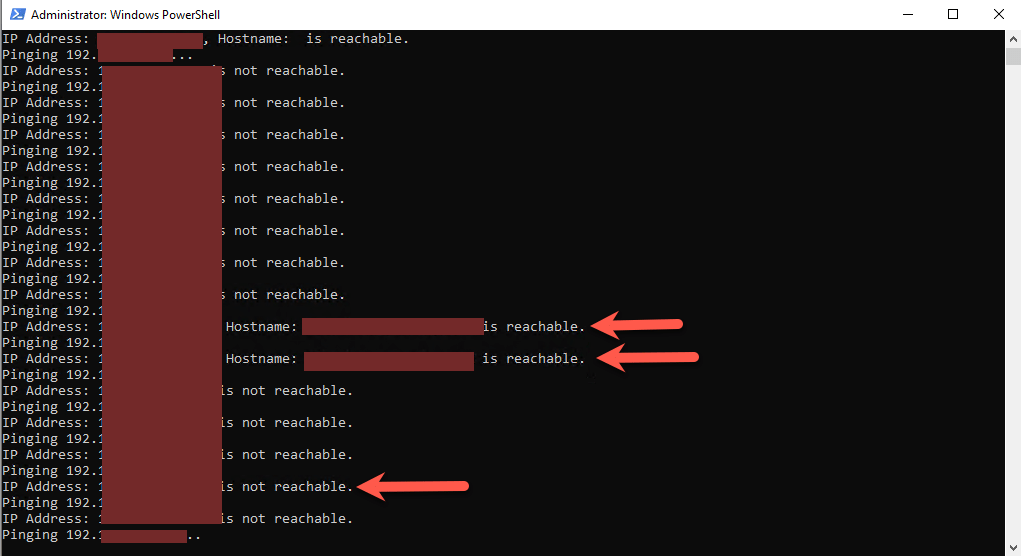
Below is the output of the script, it runs at a good speed and displays the information in the PowerShell window, you will notice the first item that does respond to Ping did not give a Hostname:
SCRIPT
The script does have two sections that need to be modified and they are as follows:
- Line 2 – The value of 255 will be used to scan all IP Addresses in the range, you can change this to 10 or whichever value you want to
- Line 3 – This is where the IP address details need to be entered. Currently it is 192.168.1., you can change this to 10.1.0. or 172.168.1.
Here is the script:
# Loop through each IP address in the range
for ($i = 1; $i -le 255; $i++) {
$ip = "192.168.116.$i"
Write-Host "Pinging $ip..."
# Run the ping command
$pingResult = Test-Connection -ComputerName $ip -Count 1 -ErrorAction SilentlyContinue
# Check if the IP address is reachable
if ($pingResult -and $pingResult.ResponseTime -ne $null) {
# Resolve the hostname for the IP address
$hostname = [System.Net.Dns]::GetHostEntry($ip).HostName
Write-Host "IP Address: $ip, Hostname: $hostname is reachable."
}
else {
Write-Host "IP Address: $ip is not reachable."
}
}Hope it helps.
