Introduction to Account Lockout Threshold
The account lockout threshold is a crucial security feature in Windows operating systems, including Windows 10 and Windows 11, designed to protect user accounts from unauthorized access. Essentially, it dictates the number of failed login attempts allowed before the system locks the account, thereby preventing further attempts. This mechanism is vital in safeguarding accounts against brute force attacks, where an attacker might try numerous password combinations to gain entry.
Implementing an appropriate account lockout threshold is a delicate balance. Setting it too low can result in frequent lockouts, causing inconvenience for legitimate users who may mistype their passwords. On the other hand, setting it too high can leave accounts vulnerable to prolonged brute force attacks, potentially compromising sensitive information. Therefore, understanding and configuring the lockout threshold is essential for maintaining both security and usability.
Moreover, the account lockout threshold works in tandem with other security settings, such as the lockout duration, which determines how long an account remains locked before it is automatically unlocked, and the reset account lockout counter, which specifies the time period after which the failed attempts counter is reset to zero. By fine-tuning these parameters, administrators can enhance the security of their systems while minimizing disruptions to legitimate users.
In the forthcoming sections, we will delve into the specifics of how to configure the account lockout threshold using PowerShell, a powerful scripting language and command-line shell developed by Microsoft. PowerShell offers a streamlined and efficient approach to managing Windows settings, making it an invaluable tool for system administrators. Whether you are working with Windows 10 or Windows 11, understanding how to use PowerShell to adjust the lockout threshold can significantly bolster your system’s security posture.
Before diving into the process of updating the lockout threshold in Windows using PowerShell, it is essential to understand the requirements and prerequisites necessary to execute this task efficiently. First and foremost, you must have administrative rights on the system where you intend to make these changes. Without administrative privileges, you will be unable to alter the security settings, including the lockout threshold.
Additionally, the version of Windows you are using is a critical factor. This guide is applicable for systems running Windows 10 and Windows 11. Ensure that your operating system is up-to-date with the latest patches and updates to avoid compatibility issues with PowerShell commands. Although PowerShell is a built-in feature in both Windows 10 and Windows 11, it is advisable to verify that you are using PowerShell version 5.1 or later. You can check your current PowerShell version by running the command $PSVersionTable.PSVersion in the PowerShell console.
Another crucial prerequisite is the presence of the necessary PowerShell modules. While the core functionalities required for updating the lockout threshold are available by default, certain advanced features might necessitate additional modules. Ensure your system has the appropriate modules installed and updated. You can use the Get-Module and Update-Module commands to manage your modules effectively.
It is also beneficial to have a basic understanding of PowerShell scripting and the specific commands you will be using, particularly the ‘Net Accounts Lockout Threshold’ command. Familiarize yourself with basic PowerShell syntax and command structures to streamline the process. Having a reliable network connection is also a prerequisite, especially if you need to download additional modules or updates.
Lastly, consider creating a backup of your current system settings. Modifying security parameters such as the lockout threshold can have significant implications. A backup ensures that you can restore your system to its previous state if something goes wrong during the process.
Understanding the ‘Net Accounts Lockout Threshold’ Command
The ‘net accounts lockout threshold’ command is a fundamental tool within the Windows operating system, particularly when configuring security settings related to user account management. This command allows administrators to specify the number of failed sign-in attempts that will trigger an account lockout, thereby enhancing the security of both Windows 10 and Windows 11 environments. By setting an appropriate lockout threshold, organizations can mitigate the risk of unauthorized access attempts through brute force attacks.
The syntax for the ‘net accounts lockout threshold’ command is straightforward:
net accounts /lockoutthreshold:
Here, represents the number of invalid logon attempts allowed before a user account is locked out. This value can be adjusted according to the specific security requirements of the organization. For instance, setting the lockout threshold to 5 will allow users up to five incorrect password attempts before their account is locked.
In addition to setting the lockout threshold, administrators also have the option to configure related parameters that further define account lockout behavior. These parameters include:
/lockoutduration: – Specifies the number of minutes a locked account will remain locked.
/lockoutwindow: – Defines the time period in which the specified number of failed logon attempts must occur to trigger the lockout.
For example, the command net accounts /lockoutthreshold:5 /lockoutduration:30 /lockoutwindow:15 sets a lockout threshold of 5 failed attempts, a lockout duration of 30 minutes, and a lockout observation window of 15 minutes.
Understanding the ‘net accounts lockout threshold’ command and its parameters is crucial for administrators aiming to bolster the security features of Windows 10 and Windows 11. By effectively using this command, they can create a more secure and resilient IT environment.
Step-by-Step Guide to Using PowerShell
Updating the lockout threshold in Windows 10 and Windows 11 using PowerShell is a streamlined process that ensures your system’s security settings are appropriately configured. Follow these steps to efficiently modify the lockout threshold using PowerShell.
1. Opening PowerShell with Administrative Privileges
First and foremost, you need to open PowerShell with administrative privileges. This is crucial because modifying system settings requires elevated rights.
To do this, follow these steps:
- Press Win + X or right-click the Start button.
- Select Windows PowerShell (Admin) from the context menu.
- If prompted by the User Account Control (UAC) dialog, click Yes to proceed.
2. Entering the Command
Once PowerShell is open with administrative privileges, you can enter the necessary command to update the lockout threshold. The command syntax is as follows:
net accounts /lockoutthreshold:value
Replace value with the desired number of invalid logon attempts before the account is locked. For example, if you want to set the lockout threshold to 5 attempts, you would enter:
net accounts /lockoutthreshold:5
Press Enter to execute the command. PowerShell will process the command and update the lockout threshold accordingly.
3. Verifying the Changes
After executing the command, it is essential to verify that the changes have been applied successfully. You can do this by entering the following command:
net accounts
Press Enter and review the output. You should see a line indicating the new lockout threshold, confirming that the update was successful. Below is an example in Windows 11:
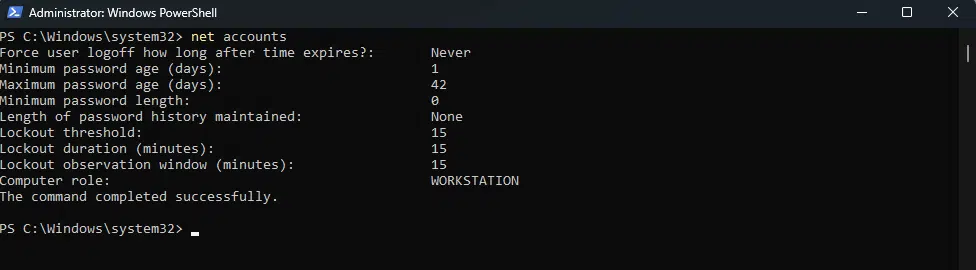
By following these steps, you can efficiently use PowerShell to update the lockout threshold on both Windows 10 and Windows 11 systems. This not only enhances your system’s security but also provides a quick and effective way to manage account policies.
Validating Your Configuration
After updating the lockout threshold in Windows using PowerShell, it is crucial to validate that the changes have been applied correctly. This ensures that the new security settings are in place and functioning as intended. To verify the current configuration, you can use several methods, including the ‘net accounts’ command, which provides a detailed overview of the account policies on your Windows system.
To check the current lockout threshold, open a PowerShell window with administrative privileges. Execute the following command:
net accounts
This command will display various account policy settings, including the lockout threshold, lockout duration, and lockout observation window. Look for the “Lockout threshold” value in the output to confirm that it matches the new setting you applied.
If the value displayed does not reflect the changes made, it is advisable to review the steps taken during the update process. Ensure that the PowerShell commands were executed correctly and that the appropriate administrative privileges were used. Additionally, verify that there were no syntax errors in the commands entered.
Another useful method to validate the configuration is by using the Group Policy Management Console (GPMC). Navigate to the “Account Policies” section under the “Computer Configuration” node and examine the “Account Lockout Policy.” Here, you can confirm that the lockout threshold aligns with the new settings. Any discrepancies should be addressed by reapplying the correct settings using PowerShell or the Group Policy Editor.
Troubleshooting tips include restarting the computer to ensure that all policy changes take effect and rechecking any group policies that might override local settings. In some cases, delays in the application of group policies may occur, so allowing some time for the changes to propagate is also recommended.
By thoroughly validating the lockout threshold configuration, you can ensure that your Windows 10 or Windows 11 system maintains the desired level of security and helps prevent unauthorized access attempts.
Best Practices for Setting Lockout Thresholds
When configuring the lockout threshold in Windows, especially through PowerShell, it’s imperative to strike a balance between security and usability. A well-thought-out lockout policy can mitigate unauthorized access attempts while ensuring legitimate users are not unduly inconvenienced. Here are some best practices to consider:
Firstly, assess the environment in which the lockout threshold will be implemented. In a corporate setting, where multiple users access the network, a lower lockout threshold (e.g., three to five failed attempts) is advisable. This minimizes the risk of brute force attacks while maintaining a manageable balance for user convenience. Conversely, in a personal or less critical environment, a slightly higher threshold may be acceptable to reduce the risk of legitimate users being locked out due to occasional mistyped passwords.
Secondly, consider the lockout duration. A shorter lockout duration (e.g., 15 to 30 minutes) is often sufficient to deter malicious activities without significantly disrupting legitimate access. For highly secure environments, a longer duration might be more appropriate, but this should be weighed against the potential for user frustration and the operational impact on productivity.
Another important practice is to monitor and review lockout events regularly. Using PowerShell commands in Windows 10 or Windows 11, administrators can easily generate reports to analyze patterns in failed login attempts. This data can provide valuable insights into potential security threats and help refine lockout policies over time.
Moreover, user education is crucial. Ensure that users are aware of the lockout policy and understand the importance of creating strong, unique passwords. Educating users on recognizing phishing attempts and other common attack vectors can further enhance the overall security posture.
Lastly, consider implementing multi-factor authentication (MFA) alongside the lockout threshold. MFA adds an additional layer of security, making it significantly harder for unauthorized individuals to gain access even if they manage to bypass the initial password lockout.
By following these best practices, organizations and individuals can effectively balance security and usability, ensuring a robust defense against unauthorized access while maintaining a user-friendly environment.
Common Issues and Troubleshooting
When updating the lockout threshold using PowerShell on Windows 10 or Windows 11, users may encounter various issues that can hinder the process. Understanding these common problems and knowing how to troubleshoot them is essential for ensuring a smooth configuration.
One frequent issue is receiving error messages such as “Access Denied” or “Insufficient Privileges.” This usually occurs when the PowerShell session does not have the necessary administrative rights. To resolve this, ensure you are running PowerShell as an administrator. Right-click on the PowerShell icon and select “Run as Administrator” before executing any commands.
Another potential problem is conflicts with existing security policies. For instance, if the account lockout threshold is being managed by Group Policy in a domain environment, local changes using PowerShell might not take effect. To troubleshoot this, review the Group Policy settings by running the “gpresult /h gpresult.html” command to generate a report. Check the report to identify any conflicting policies and adjust them accordingly.
Additionally, users might face issues if the system’s security baseline configuration does not align with the intended changes. Security baselines are predefined configurations that enforce certain security standards on Windows systems. If an organization’s security baseline mandates a specific lockout threshold, manual changes via PowerShell could be overridden. To address this, consult with your IT department or review the security baseline documentation to ensure compatibility.
In practical scenarios, users have reported issues where the lockout threshold settings are not applied immediately. This can be due to cached credentials or delayed policy propagation. A simple fix is to restart the computer or force a policy refresh using the “gpupdate /force” command. This ensures that all new settings are applied correctly.
By being aware of these common issues and knowing how to troubleshoot them, users can effectively manage the lockout threshold settings on Windows 10 and Windows 11 using PowerShell, ensuring a secure and efficient computing environment.
Conclusion and Additional Resources
In conclusion, updating the lockout threshold in Windows using PowerShell is a straightforward yet crucial step in securing your system. By leveraging the ‘Net Accounts Lockout Threshold’ command, administrators can effectively manage account lockout settings, thereby enhancing the overall security posture of both Windows 10 and Windows 11 environments. This process not only helps in mitigating unauthorized access attempts but also ensures that legitimate users are not unduly inconvenienced by frequent lockouts.
For those who wish to dive deeper into the subject, several resources are available. The official Microsoft documentation provides comprehensive guidelines on using PowerShell for a variety of administrative tasks, including account management. Additionally, community forums such as Microsoft Tech Community and Stack Overflow offer a wealth of user-generated insights and troubleshooting tips, making them invaluable for both novice and experienced administrators.
For further reading, consider exploring the following resources:
- Microsoft PowerShell Documentation
- Microsoft Account Lockout Threshold Documentation
- Microsoft Tech Community
- Stack Overflow
- Reddit SysAdmin Community
We encourage you to implement these changes and take proactive steps in securing your Windows systems. Staying informed and utilizing available tools, such as PowerShell, can greatly enhance your ability to manage and protect your network effectively. Your feedback and experiences are valuable, so feel free to share your insights in the comments section below or engage with the community in the forums mentioned above.
We hope you find it helpful.
