In a previous blog post, we searched for a specific keyword in PowerShell and displayed it in PowerShell directly.
In this blog post, we will be looking for a specific Event ID that is triggered when an account cannot be logged onto and sometimes you can see the calling computer which will help when accounts are either compromised or attacked.
Event ID 4625 is an event that may come up if a user does put in the wrong password however if an attacker is password spraying accounts with different passwords, it will trigger these event logs in the Security Logs. I put together a script that will can go and search multiple computers for this event and display the information for you.
Below is an example of an event that occurred on my lab Exchange 2019 Server after I tried to brute force OWA:
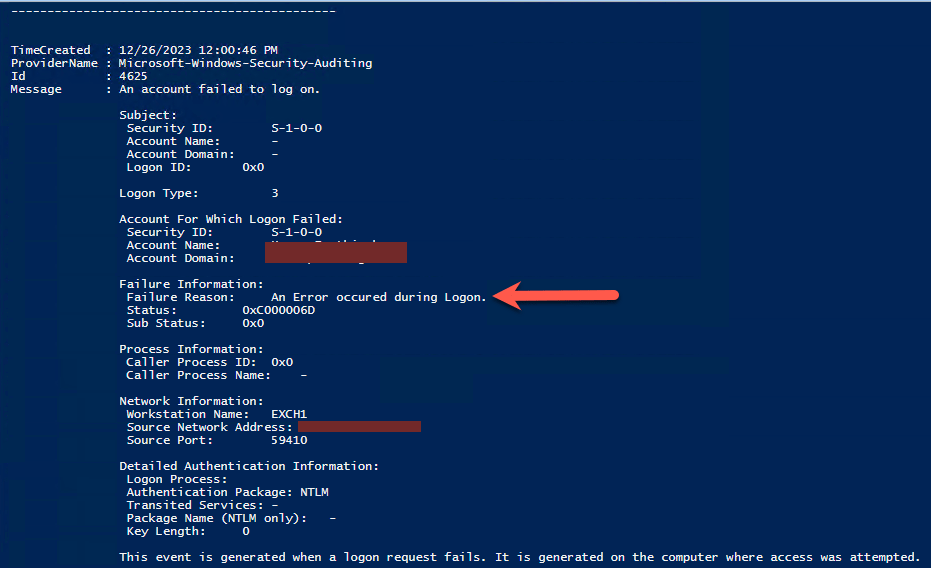
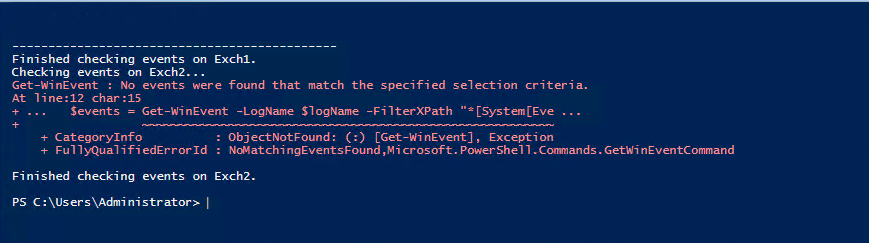
It displays what you would typically see in Event Viewer on the machine you are looking at. If no events are found, it will display an error that no logs are found as shown below:
SCRIPT
The script has a section that needs to be modified and it is the following:
- $remoteComputers
You can specify all the computers here, separated by comma, an example would look like this:
- ‘Server1’, ‘Server2’
Here is the script, you can modify the script if you want to export the file to CSV rather than displaying it on the screen.
# Define the log name and event ID
$logName = 'Security'
$eventID = 4625
# Specify the remote computer name or IP address
$remoteComputers = 'Server1', 'Server2'
foreach ($computer in $remoteComputers) {
Write-Host "Checking events on $computer..."
# Get events from the Security log with Event ID 4625 on the remote computer
$events = Get-WinEvent -LogName $logName -FilterXPath "*[System[EventID=$eventID]]" -MaxEvents 10 -ComputerName $computer
# Display information for each event on the remote computer
foreach ($event in $events) {
$eventTime = $event.TimeCreated
$eventID = $event.Id
$message = $event.Message
# Extract relevant information from the event message
$userName = ($message -match 'Account For Which Logon Failed:\s+\w+\\(\S+)')[1]
$failureReason = ($message -match 'Failure Reason:\s+(\S+)')[1]
# Display information in a nice format
$event | format-list | out-string | Write-Host
Write-Host "---------------------------------------------"
}
Write-Host "Finished checking events on $computer."
}You can run this directly from PowerShell ISE or save the script and just run it from PowerShell.
Hope it helps.
