In my previous blog post, we looked at creating a self signed certificate using PowerShell (3x Liner). The certificate obviously is not what a professional cert is, one thing missing is the “Friendly Name” which can be changed in the MMC and certificates snapin.
I took the certificate and created a PowerShell Script to Import it into my Exchange 2019 Server and assign services to it. Below is the output from the script:
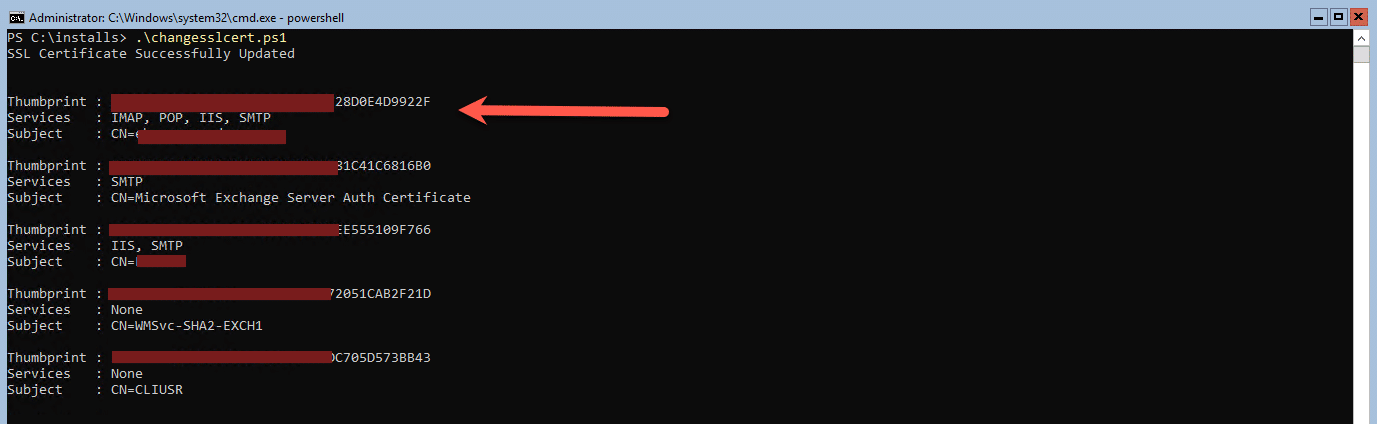
The first certificate Thumbprint is the one that was imported and services (IIS,IMAP,SMTP,POP) assigned to it.
Script
Below is the script, it has some parts that require manual change and these are as follows:
- $CertPath – Where the certificate is saved to
- $CertPassword – The password assigned to the .PFX certificate
- $CertFriendlyName – The Friendly Name provided to your SSL Certificate (commented out because it didn’t apply in my scenario)
- $Services – Specify the services required or accept the default set
Here is the script:
# Import the Exchange module
Add-PSSnapin Microsoft.Exchange.Management.PowerShell.SnapIn
# Replace these values with your actual certificate information
$certPath = "C:\Installs\SSLCert.pfx"
$certPassword = "Password123"
#$certFriendlyName = "YourCertificateFriendlyName"
$services = "IIS,SMTP,POP,IMAP"
# Import the certificate
$cert = Import-PfxCertificate -FilePath $certPath -CertStoreLocation Cert:\LocalMachine\My -Password (ConvertTo-SecureString -String $certPassword -AsPlainText -Force)
# Assign the certificate to the appropriate services
Enable-ExchangeCertificate -Thumbprint $cert.Thumbprint -Services $services
Write-Host "SSL Certificate Successfully Updated"
Get-ExchangeCertificate | fl Thumbprint,Services,Subject
Once the script has completed, you can validate the change by going to IIS and looking at the bindings for the “Default Web Site” on your Exchange Server.
Hope it helps.
