In Exchange 2016 or 2019, you have the ability to accept TLS connections on a receive connector from a particular set of IP Addresses or single IP and have it use an SSL certificate.
What I have seen happen is that receive connectors are not configured correctly in a sense, they are missing some sections. In this article we will cover the steps to ensure that you are presented with the correct certificate from the partner server side.
In a previous article, we set the TLS certificate name on a receive connector. We will be configuring the following:
- Creating a receive connector with the Partner auth method.
- Adding in a remote IP for the server that will be sending.
- Configuring TransportConfig parameters.
- Set the RequireTLS on the receive connector.
- Test using OpenSSL
Let’s start this in reverse. Open up the Exchange Management Shell and run the following command:
- Set-ReceiveConnector “Connector Name” -RequireTLS $True
I have it already set in my lab hence the warning but you should not see anything once set. You can run the Get-ReceiveConnector command to verify that it is enabled as below:
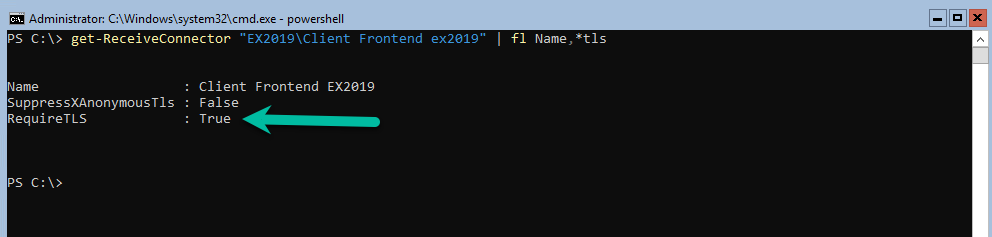
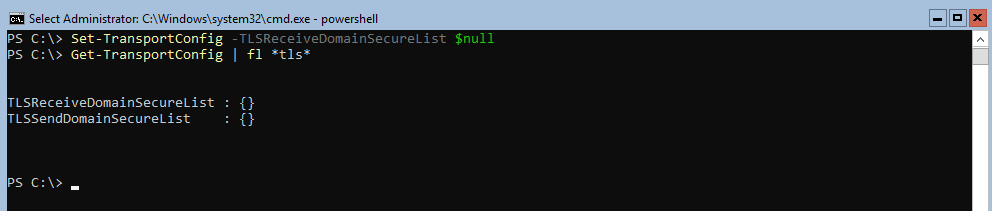
The next step we are going to configure the following value “TLSReceiveDomainSecureList” which can be found in the TransportConfig command as shown below:
- Get-TransportConfig | fl *tls*

We can now run the set command and add in a domain, here is an example of the command:
- Set-TransportConfig -TLSReceiveDomainSecureList “Collaborationpro.com”
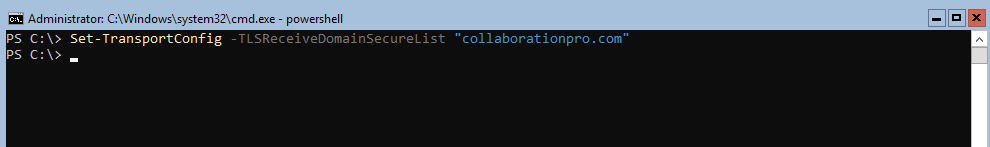
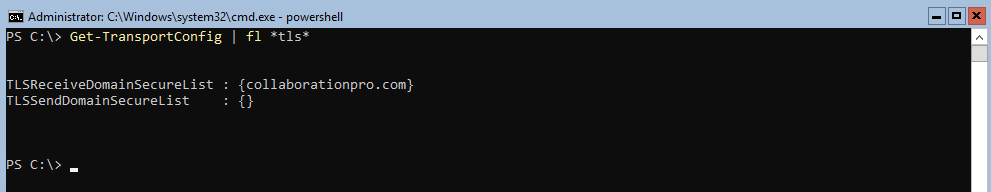
If you now run the Get command in the previous step, it should be configured, below is what it should look like:
If you want to revert the change at any point, you can run the following command:
- Set-TransportConfig -TLSReceiveDomainSecureList $null
We can now move onto creating our Partner Receive Connector. Open up the Exchange Admin Center and once you have logged in, click on Mail Flow and then on Receive Connectors.
On the Receive Connector page, select the server from the drop-down list if you have multiple servers and where you want the receive connector to reside and then click the + button to open up the Wizard.
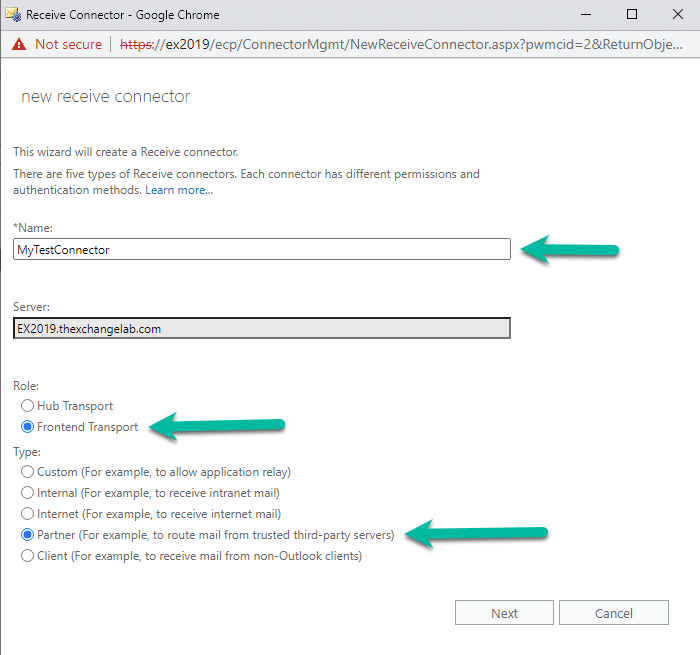
On the “New Receive Connector” Page, we need to set the following:
- Name
- Role (It will be Frontend Transport in our case)
- Type (Will be Partner)
Below is what the first page looks like:
Click Next. On the next page, you can set your adapter bindings and IP addresses:
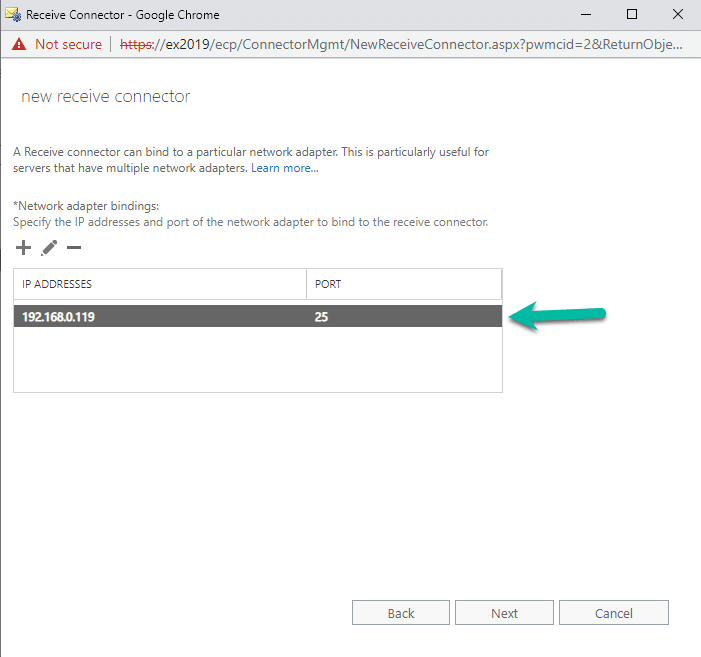
In the example above, I clicked the pencil and changed all IP’s to a specific IP. If you want to add in a different port like 587 you can do so as well. Once done, you can click Next.
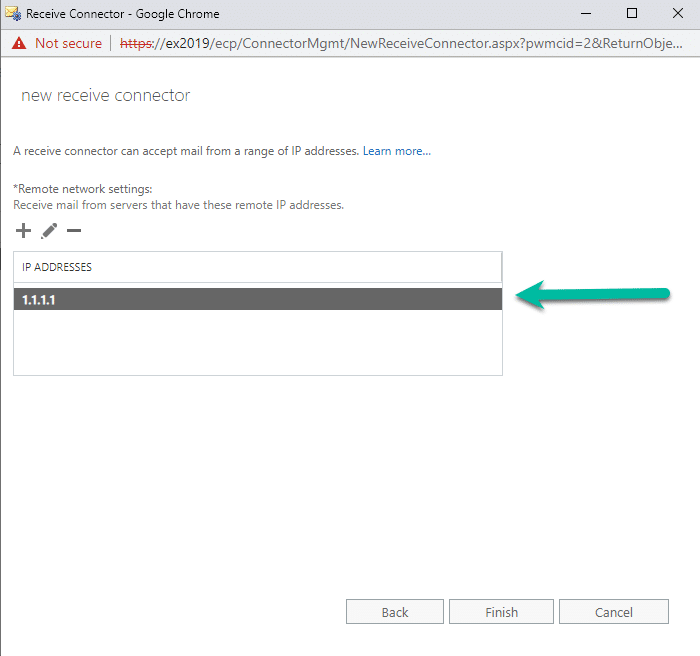
On the remote network settings, I clicked on the pencil again and specified an ip (1.1.1.1 is not real, but you get the idea). Once you have entered in all the remote partner IP’s, you can click Finish.
Back in the Exchange Admin Center, you can now double click on your Receive connector and if you click on the scoping tab, you can enter in the FQDN of the certificate and you can also change the TLS certificate name as we did in a previous post.
Testing
We can now use a tool called OpenSSL to test and make sure we get the correct certificate. I downloaded version 3.0.1 x64 and installed it in my lab. In PowerShell you can navigate to where the openssl.exe file is located and run the following command:
- .\openssl.exe s_client -connect 192.168.0.119:25 -starttls smtp
You should see the below information, showing you the certificate used which should be your SSL certificate:
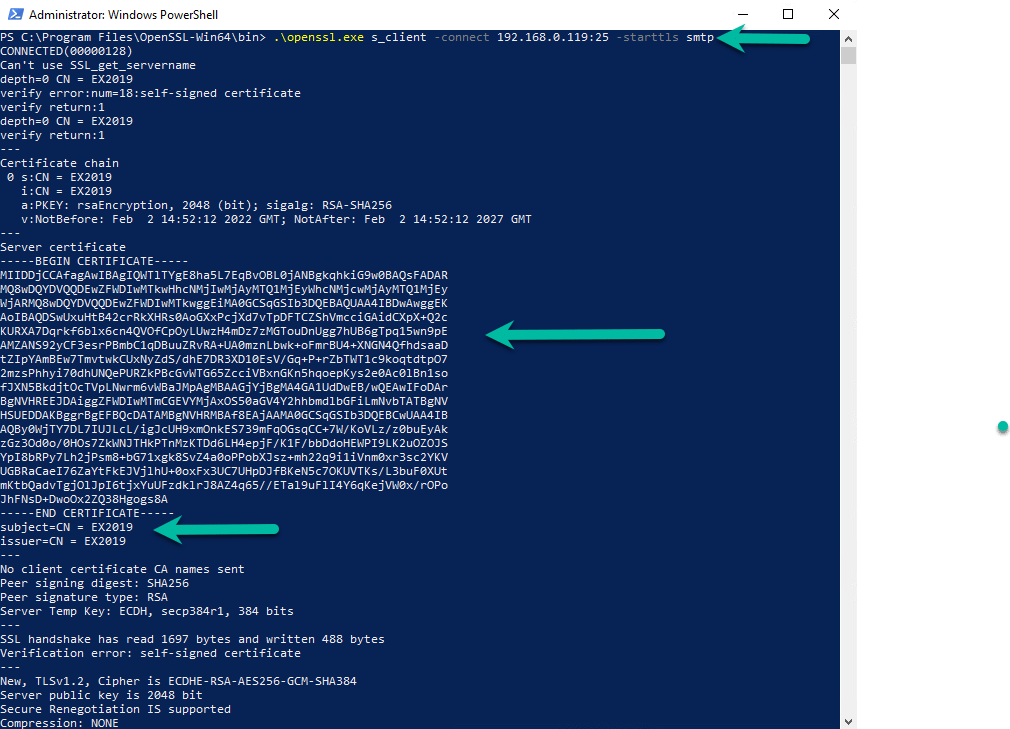
I used my internal IP to show you how it runs but you can put in an external IP as well and change the port to 587 which should give you the same certificate. If the partner organization is happy with the result, you can start start sending email and analyse the headers to make sure that everything is correct.
Hope it helps.
